Assume the following scenario:
- The certification authority is configured to send e-mail notifications about the events on the certification authority only using the SMTP Exit module.
- The configured SMTP server is not always reliably accessible, for example, because it is not designed to be highly available.
- If the SMTP server fails, the certificate authority will operate very slowly because the email notifications cannot be delivered. In some circumstances, the certificate authority service will no longer start.
Do you know TameMyCerts? TameMyCerts is an add-on for the Microsoft certification authority (Active Directory Certificate Services). It extends the function of the certification authority and enables the Application of regulationsto realize the secure automation of certificate issuance. TameMyCerts is unique in the Microsoft ecosystem, has already proven itself in countless companies around the world and is available under a free license. It can downloaded via GitHub and can be used free of charge. Professional maintenance is also offered.
The underlying problem is that the certificate authority's e-mail notification function has no features to compensate for an SMTP server failure.
This problem can be circumvented by installing a local SMTP server on the certification authority. The local SMTP server receives the emails from the certification authority and caches them when the SMTP server on the network is unreachable.
Warning: This option also brings some disadvantages - the SMTP server of Windows Server 2019 is a very, very old IIS 6.0 component, and as a dependency a web server is always installed as well, which is not recommended on a certificate authority due to the increased attack surface. A better solution would be to implement a central database for evaluating event logs (for example, Microsoft Azure Log Analytics), and set up email notification at this point.
The SMTP server role can be installed with the following Windows PowerShell command:
Add-WindowsFeature SMTP-Server -IncludeManagementTools
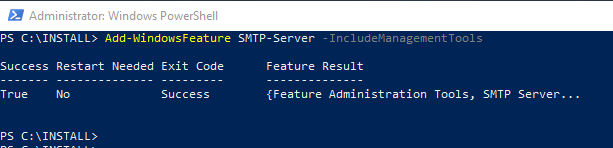
The SMTP server is administered with the IIS 6.0 Manager.
Right-click on the default entry and then click on Properties to open the configuration.
It must be defined which hosts are allowed to send emails via this SMTP server. This should only be the host itself. In the Access tab, the settings can be found in the Relay restrictions.
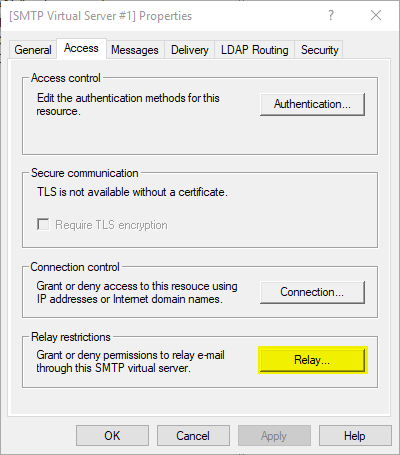
Unfortunately, the SMTP server cannot be bound to the local loopback address 127.0.0.1, but only to either all IP addresses or specific IP addresses that are present on a network card. Due to the restrictions described above, it is important to ensure that the local firewall does not allow connections to ports 25 (SMTP) and 80 (HTTP).
The relay restrictions are set so that only the local host (the IP address of the network card must be entered, not the loopback address) may send e-mails.
The release after authentication is switched off.
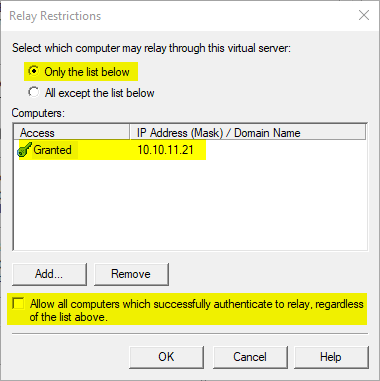
For forwarding to the internal mail gateway to work, a mail exchanger (MX) record must be configured in the internal DNS for the recipient domain, since you cannot define forwarding rules in the IIS SMTP Server.
Now the SMTP Exit module of the certificate authority can be configured to send the e-mail notifications to the locally installed SMTP server.
certutil -setreg exit\smtp\SMTPServer {Ip address of the certification authority}
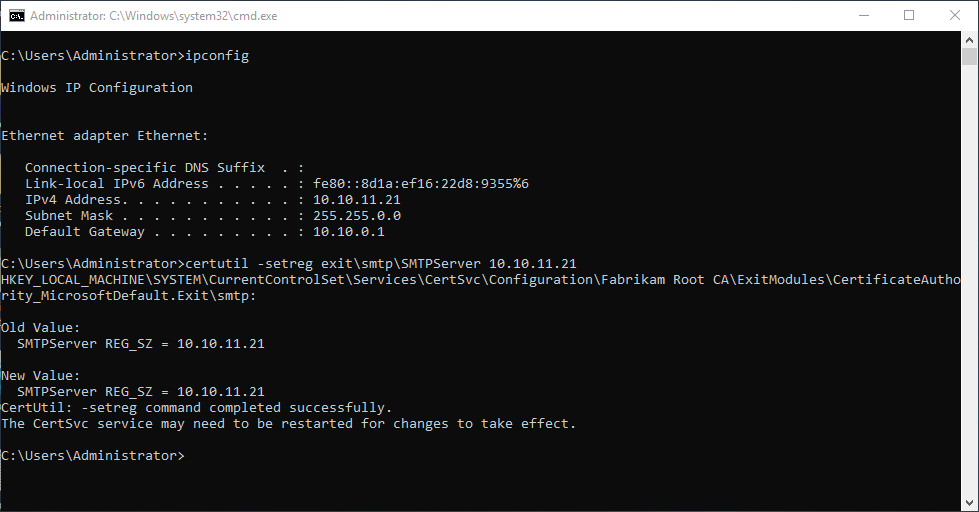
For the changes to take effect, the Certification Authority service must be restarted.
The queue of the local SMTP server is located at C:\inetpub\mailroot\Queue and can be viewed there.
2 thoughts on “Kombinieren des SMTP Exit Moduls mit einem lokalen SMTP-Server für erhöhte Ausfallsicherheit”
Comments are closed.