Someone recently approached me with an interesting problem.
A certification authority has been installed. Linux is used as the basis, i.e. (presumably) OpenSSL. The revocation lists work on Linux clients, but are not accepted by Windows systems. The following error message always appears when checking the revocation lists.
0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE) -- 2148081683 (-2146885613)
Text der Fehlermeldung: Die Sperrfunktion konnte die Sperrung nicht überprüfen, da der Sperrserver offline war.
The error message reads as follows:
0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE) -- 2148081683 (-2146885613)
The revocation function was unable to check revocation because the revocation server was offline.
As you can see, the test certificate is accepted perfectly via the Windows shell dialog.
However, we get to the bottom of the matter and check the addresses contained in the certificate for the certification authority certificate and certificate revocation lists.
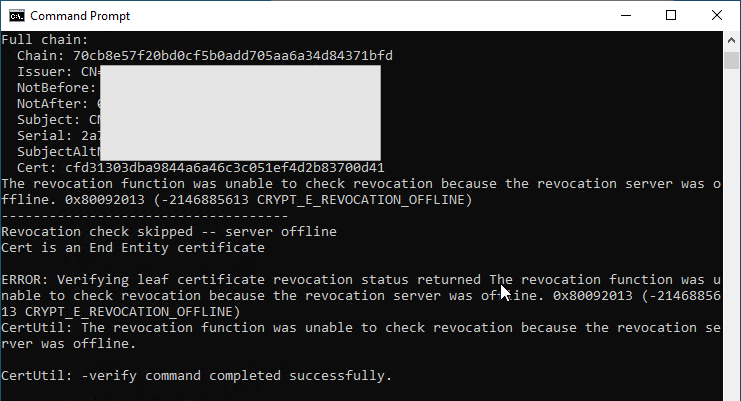
certutil -verify -urlfetch test.cer
Here we encounter the error code CRYPT_E_REVOCATION_OFFLINE.
ERROR: Verifying leaf certificate revocation status returned The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE)
CertUtil: The revocation function was unable to check revocation because the revocation server was offline.
To gain a deeper insight into what is happening in the background, we activate logging for the CryptoAPI (CAPI).
To do this, we go to the event display under "Applications and Services Logs" - "Microsoft" - "Windows" - "CAPI2".
The CAPI2 log is deactivated by default as it logs a large number of entries. We are activating it temporarily.
Now we reproduce the error with certutil and then deactivate the log again.
In CAPI2 Log we now find events of the category "Reject Revocation Information".
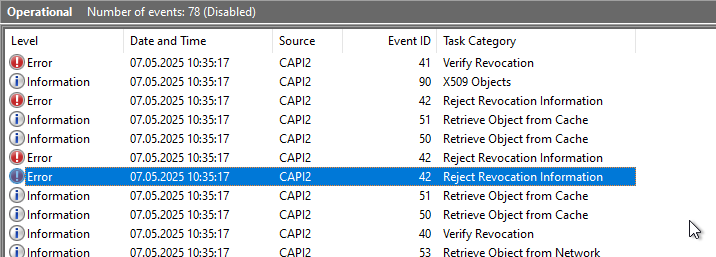
If we take a look at the details, we see that the blacklist could be downloaded, but the check was apparently not successful.
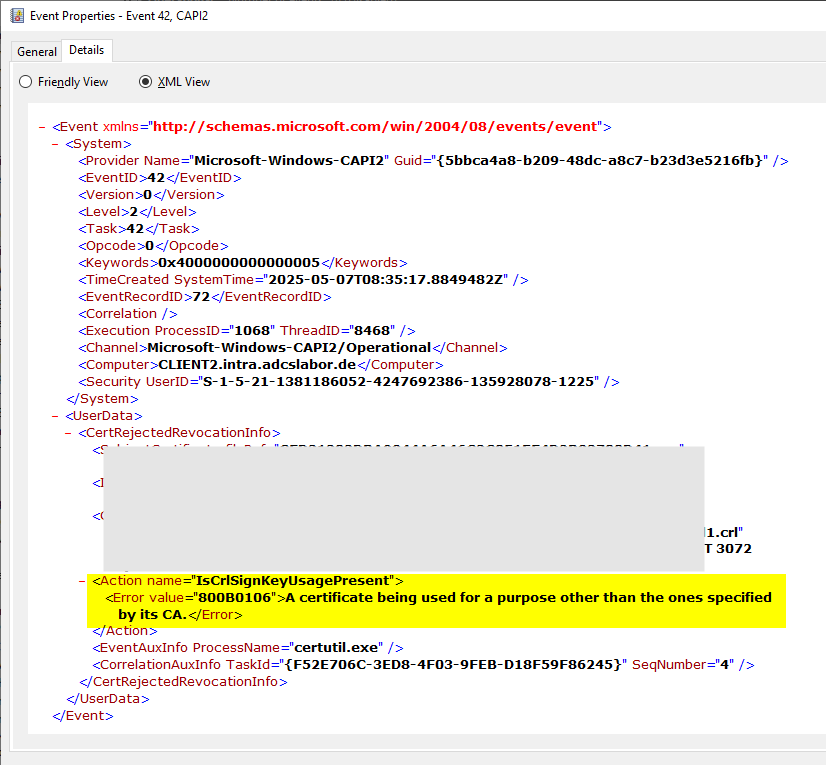
The error message reads:
A certificate being used for a purpose other than the ones specified by its CA.
This means that the certificate revocation list was issued by a certification authority that is not authorized to do so.
So let's take a look at the certification authority certificate.
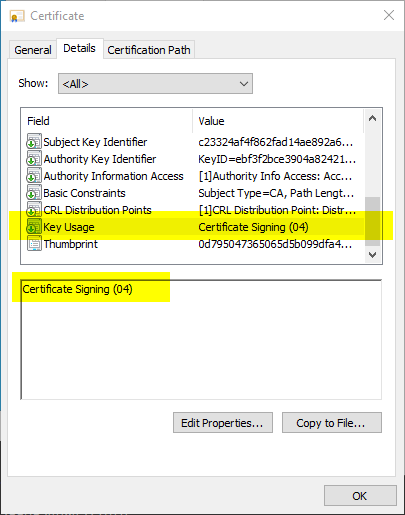
In the Key Usage certificate extension we note that the certification authority certificate is only available via the Key Usage keyCertSign (0x4), but not cRLSign (0x2) is available.
The certification authority is therefore not authorized to issue certificate revocation lists at all. The CAPI recognizes this and accordingly refuses to accept the revocation list as valid.
Conclusion
The description test of the error code CRYPT_E_REVOCATION_OFFLINE indicates that it cannot be downloaded, but in practice this error code can mean much more, for example:
- The certificate revocation list cannot be downloaded
- The certificate revocation list is not yet or no longer valid
- The certificate revocation list cannot be verified
It also shows that Microsoft Active Directory Certificate Services protects us from many potential stumbling blocks in the PKI area with sensible default settings.