| Event Source: | Microsoft-Windows-CertificationAuthority |
| Event ID: | 77 (0x4D) |
| Event log: | Application |
| Event type: | Warning |
| Symbolic Name: | MSG_POLICY_LOG_WARNING |
| Event text (English): | The "%1" Policy Module logged the following warning: %2 |
| Event text (German): | The policy module "%1" has logged the following warning: %2 |
Parameter
The parameters contained in the event text are filled with the following fields:
- %1: PolicyModuleDescription (win:UnicodeString)
- %2: WarningMessage (win:UnicodeString)
Example events
The "Windows default" Policy Module logged the following warning: The Active Directory connection to DC01.intra.adcslabor.de has been reestablished to DC01.intra.adcslabor.de.
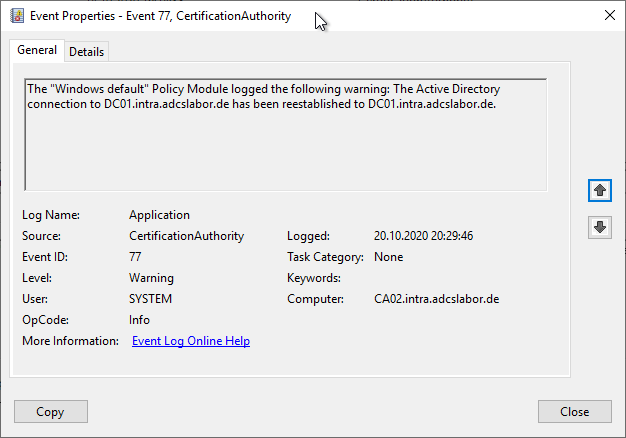
The "Windows default" Policy Module logged the following warning: The Active Directory connection to ??? has been reestablished to DC01.intra.adcslabor.de.
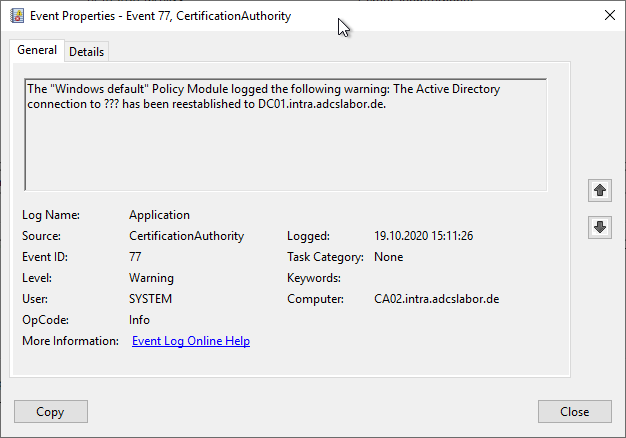
The "Windows default" Policy Module logged the following warning: The ADCSLaborSMIME Certificate Template could not be loaded. Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND).
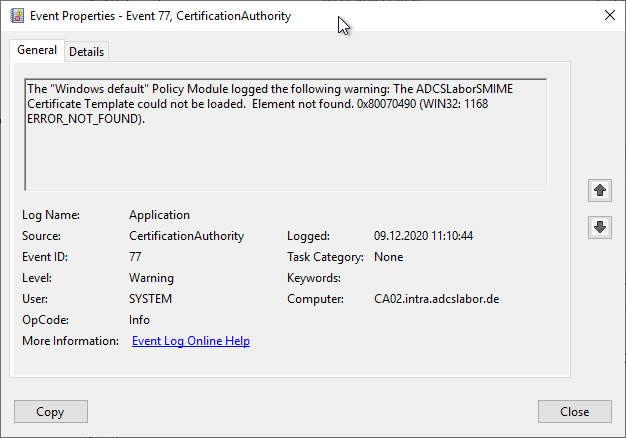
The "Windows default" Policy Module logged the following warning: Active Directory Certificate Services is configured to use LDAP referrals to request user data from the Active Directory directory service.
Description
Error messages of the configured policy module.
The Active Directory connection to [...] has been reestablished to [...].
This event is triggered when the current LDAP connection of the certification authority's policy module is renewed. In most cases, it is part of the standard behavior of the Microsoft certificate authority and can be safely ignored if it occurs only sporadically.
See also Event no. 91.
The [...] Certificate Template could not be loaded. Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND).
Occurs when a certificate template was published on the certificate authority that no longer exists in Active Directory.
Also occurs when the certificate authority does not have read permission on a published certificate template. By default, the certificate authority obtains read permission through the Authenticated Users entry in the certificate template's security settings.
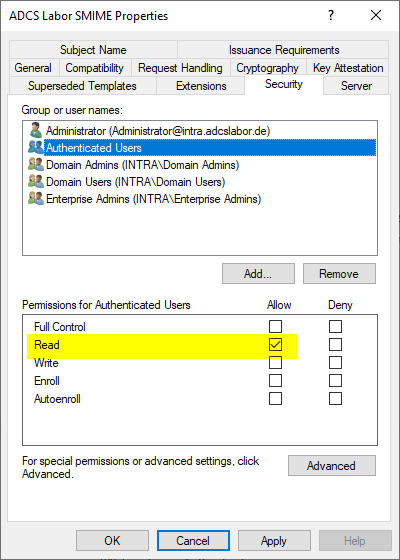
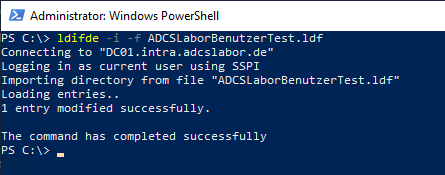
A deleted certificate template can be restored (if available) from an LDIF export with the following command:
ldifde -i -f {filename>
Active Directory Certificate Services is configured to use LDAP referrals to request user data from the Active Directory directory service.
Reported when the EDITF_ENABLELDAPREFERRALS flag is set, for example because the certification authority is participating in cross-forest autoenrollment. The settings can be viewed with the following command:
certutil -v -getreg Policy\EditFlags
Safety assessment
The security assessment is based on the three dimensions of confidentiality, integrity and availability.
The event "The Active Directory connection to [...] has been reestablished to [...]." does not affect confidentiality, integrity, or availability.
The event "The [...] Certificate Template could not be loaded. Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND)." has an impact on availability, because no certificates can be issued from this certificate template. For this reason it should be monitored and alerted.
Microsoft rating
Microsoft evaluates this event in the Securing Public Key Infrastructure (PKI) Whitepaper with a severity score of "Low".
Related links:
- Overview of Windows events generated by the certification authority
- Overview of audit events generated by the Certification Authority
External sources
- Event ID 77 - AD CS Policy Module Processing (Microsoft)
- Securing Public Key Infrastructure (PKI) (Microsoft)
2 thoughts on “Details zum Ereignis mit ID 77 der Quelle Microsoft-Windows-CertificationAuthority”
Comments are closed.