Often, problems with the public key infrastructure can be found in the underlying network - for example, if a firewall rule is missing from the network.
Thus, it is helpful if one is able to record network traffic in order to analyze it. Excellent tools exist for this purpose, such as Wiresharkbut these require that an installation be made on the system in question, which cannot and should not be done easily on a production system.
Fortunately, the Windows Server operating system has a built-in mechanism to capture network packets. However, the resulting files are not compatible with Wireshark. The Microsoft proprietary tool, Message Analyzer, was discontinued on Nov 25, 2019 and the download links removed.
The following therefore describes how such a recording can be generated and subsequently converted into a Wireshark-compatible format in order to be able to analyze the recording away from the server in question.
On the PKI system in question, a packet capture is started as an administrator with the following command line command:
netsh trace start persistent=yes capture=yes tracefile={path-to-task-file}.etl
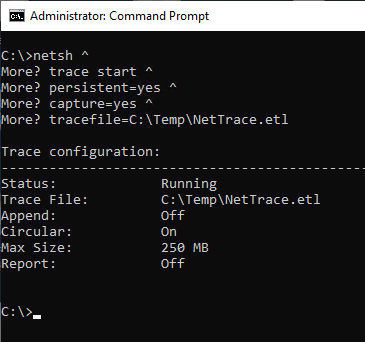
If the "tracefile" parameter is not specified, a file is automatically created in the user's temp directory.
After a short waiting period one can start reproducing the error. If this was finished successfully, the recording can be terminated with the following command line command:
netsh trace stop
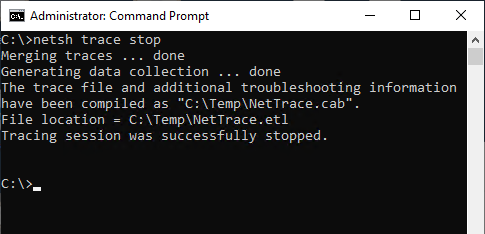
The created file can now be used either on the same system or on another system with the free Microsoft program etl2pcapng be converted to a Wireshark-compatible format.
etl2pcapng {ETL file}.etl {PCAPNG file}.pcapng
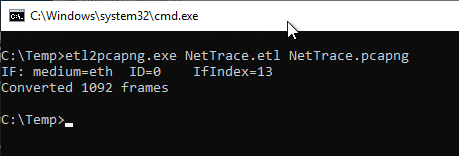
The .pcapng file generated in this step can now be opened and analyzed with Wireshark.
Filtering the recorded data
In case a network firewall silently drops the outgoing data packets, an appropriate filter could look like the following, for example:
| Action | Syntax |
|---|---|
| Show traffic from a specific source system only | ip.src == {IP-address-of-source-system} |
| Show traffic to a specific target system only | ip.dst == {IP-address-of-source-system} |
| Show only initiated TCP connections | tcp.flags.syn == 1 |
Example:
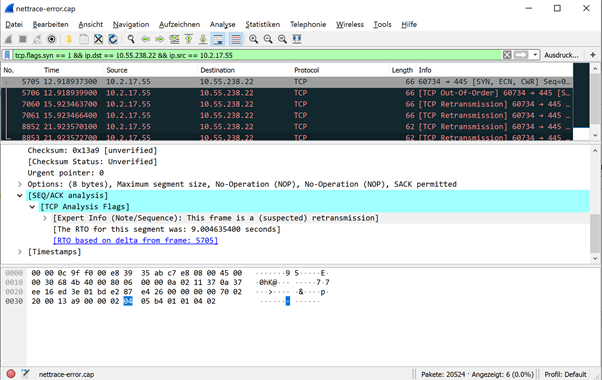
tcp.flags.syn == 1 && ip.dst == {IP-address-of-target-system} && ip.src == {IP-address-of-source-system}
If the filter is now applied to the .pcapng file, the previously described case of a network firewall silently dropping outgoing packets would show up as follows, for example (packets with the SYN flag set repeatedly appear, Wireshark suspects retransmission):
Related links
External sources
- microsoft/etl2pcapng (GitHub)
- No Wireshark? No TCPDump? No Problem! (SANS ISC InfoSec Forums)
- So you want to use Wireshark to read the netsh trace output .etl? (Microsoft TechNet Blogs, archive link)
- Microsoft Message Analyzer Blog (Microsoft)
One thought on “Netzwerkprobleme mit Wireshark analysieren, ohne Software auf produktiven Systemen installieren zu müssen”
Comments are closed.